Hades is created to put your skills in Active Listing enumeration & exploitation, lateral motion, and privilege escalation to your take a look at in a modest business network.
Committed Labs Manage the most recent assaults and cyber threats! Be certain learning retention with palms-on techniques development by way of a
Be a part of our mission to create a safer cyber environment by building cybersecurity teaching pleasurable and available to Anyone. No boundaries, no constraints.
Les geeks traînent avec d’autres geeks. Le bouche à oreille est toujours une bonne façon de trouver des gens talentueux avec qui travailler.
The scope decides whether or not a company is interested in a selected vulnerability. Once you have verified the program will settle for the vulnerability, you'll want to submit The difficulty to the program.
The goal is to realize a foothold on The inner network, escalate privileges and finally compromise the complete infrastructure, though collecting various flags together the way in which. State-of-the-art Difficulty
Sign up for our mission to produce a safer cyber earth by building cybersecurity teaching enjoyment and obtainable to All people. No USDT recovery services boundaries, no constraints.
Nous sommes ravis de vous offrir divers moyens de nous joindre. Que ce soit pour des thoughts, des commentaires ou des collaborations, n’hésitez pas à entrer en Speak to avec nous. Veuillez choisir l’choice qui vous convient le mieux :
APTLabs is a contemporary and extremely demanding lab that gives the opportunity to hone your investigation skills and compromise networks without having applying any CVEs.
Par Engager hacker France possibility, cela signifie que si vous voulez engager un hacker ou que vous cherchez des collaborations potentielles avec un budget réduit, vous copyright recovery service trouverez vraisemblablement quelqu’un qui voudra bien vous aider. Alors comment le trouver ? Voici ce qu’en dit Aron Pilhofer du The big copyright recovery apple Situations :
Why hack by yourself when you can perform like a crew and receive additional dollars? Quickly collaborate on experiences to share bounties though Discovering and earning alongside one another.
Ascension is created to exam your abilities in enumeration, exploitation, pivoting, forest traversal and privilege escalation within two compact Active Directory networks.
The goal is to get a foothold on The interior network, escalate privileges and finally compromise the area whilst collecting many flags along the way. Highly developed Problem
Dedicated Labs Handle the most recent attacks and cyber threats! Guarantee Finding out retention with palms-on techniques progress via a
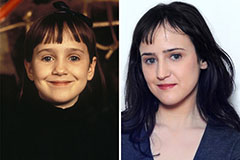 Mara Wilson Then & Now!
Mara Wilson Then & Now! Molly Ringwald Then & Now!
Molly Ringwald Then & Now! David Faustino Then & Now!
David Faustino Then & Now! Robin McGraw Then & Now!
Robin McGraw Then & Now! Rossy de Palma Then & Now!
Rossy de Palma Then & Now!